24.05.2022 - The number of reports received by the NCSC was high last week. The main reason was apparent threat emails from the police. A user of Microsoft Outlook was also «warned», in an email purporting to come from Microsoft, about unusual sign-in activity from Moscow. Closer investigation by the NCSC revealed this to be a phishing attempt. Thanks to the use of a Sender Policy Framework, this message was identified as a phishing email and automatically moved to the spam folder.

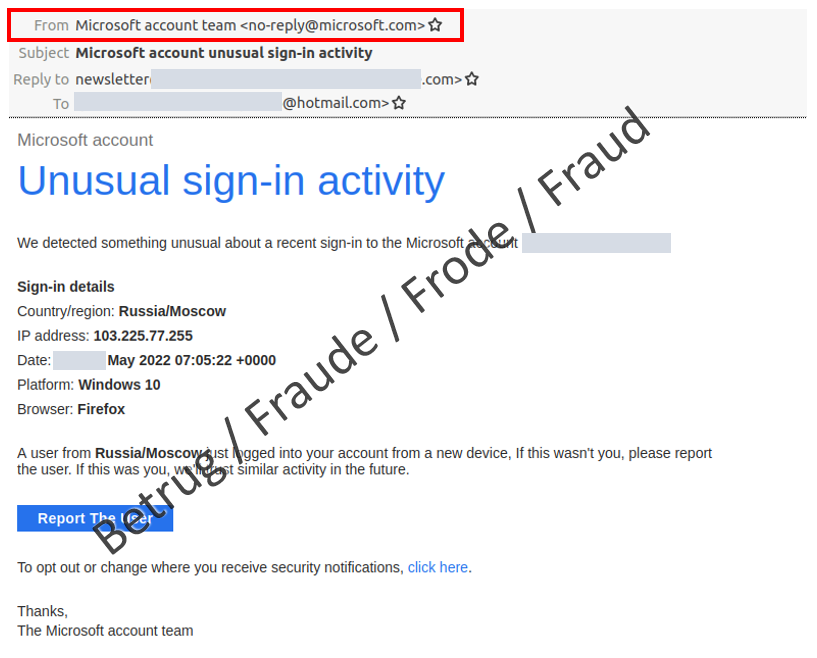
Message about unusual sign-in attempts from Moscow
If Microsoft detects an attempt to sign into an email account from a new location or device, the user receives an email notification for security reasons. This type of notification is being faked by attackers and exploited to send phishing emails.
Last week, the NCSC received a report of such a fraudulent email, with the subject line «Microsoft account unusual sign-in activity», sent from «no-reply@microsoft.com». However, when the email is opened, the eye is immediately drawn to the line «Country/region: Russia/Moscow», not least because of the current conflict in Ukraine. The person who reported the incident found it strange that Outlook had already moved the mail to the spam folder. According to the displayed sender information, the email came from Microsoft itself.
A check of the email revealed that it did not come from Microsoft and would turn out to be a phishing attempt. However, in a departure from the fraudsters' usual practice, the "Report The User" link and the link for changing the security notifications did not lead directly to the phishing website but instead opened a reply email. Yet this reply email was not addressed to Microsoft but rather to Google email addresses created especially for the purpose. The NCSC is unsure what the attackers will do if they receive a reply. Either they will send a link to a fake Microsoft login page or they will send a second email to try and obtain login data.
The IP address displayed in the email leads to an Indian telecoms provider in Kolkata – not to Moscow. People who are familiar with network technology will also note that the displayed IP address is the broadcast address of the network and cannot be used for logins.
When the email's source code is examined, it becomes clear that a tracking pixel is uploaded when the recipient (unwittingly) opens the email.
This allows the senders to tell whether the message has been opened by the recipient, and is often used to verify email addresses when sending spam.
It is unclear whether the attackers deliberately chose Moscow in Russia as the sender location. However, phishers often exploit current affairs to lend credence to their story. The war in Ukraine is also being misused by fraudsters to create uncertainty among email recipients.
The email is clearly aimed at users of Microsoft Outlook365. However, Outlook's spam detection program identified the email as a phishing attempt and moved it to the spam folder despite the sender address, which was fake. Thanks to a simple technique called Sender Policy Framework (SPF), an email is classified as fake as soon as the sender is not from the claimed location.
- Emails that are moved directly to the spam folder should be treated with great caution. Do not click on links or answer the email under any circumstances;
- In your email client, activate the function "Do not download data when opening emails";
- Just like the sender in a conventional letter, senders in emails can be freely made up – so do not trust them;
- Report such emails to the NCSC, ideally as the original, i.e. together with the email header.
Current statistics
Last week's reports by category:
Last modification 24.05.2022