09.01.2024 - Previous weekly reviews have already highlighted the different ways in which scammers try to gain direct access to your device. In the current NCSC weekly review, another duplicitous method is explained.

The beginnings
For years, there has been one main modus operandi for the phenomenon known as ‘fake support calls’: random phone numbers are called via foreign call centres. The person called is told in English (rarely also in German or French) that their computer is infected and needs to be cleaned. Such calls have not ceased altogether, but are becoming increasingly rare. The fraud attempt is transparent and requires a great deal of effort on the part of the fraudsters as every call is personally initiated and processed by a call centre agent.
The development
In order to minimise their own costs, the scammers have resorted to having the initial call made automatically. Only those callers who follow the automated greeting (‘Press 1’) are subsequently connected to a fraudulent agent. This variant was responsible for the high number of reports received by the NCSC last year.
The variant in French-speaking Switzerland
Another variant of this scam is most likely perpetrated by a different criminal organisation, but the aim is the same: to install remote maintenance software on the victim's device so that the criminals can ultimately gain access to payment applications or information (e-banking, credit cards).
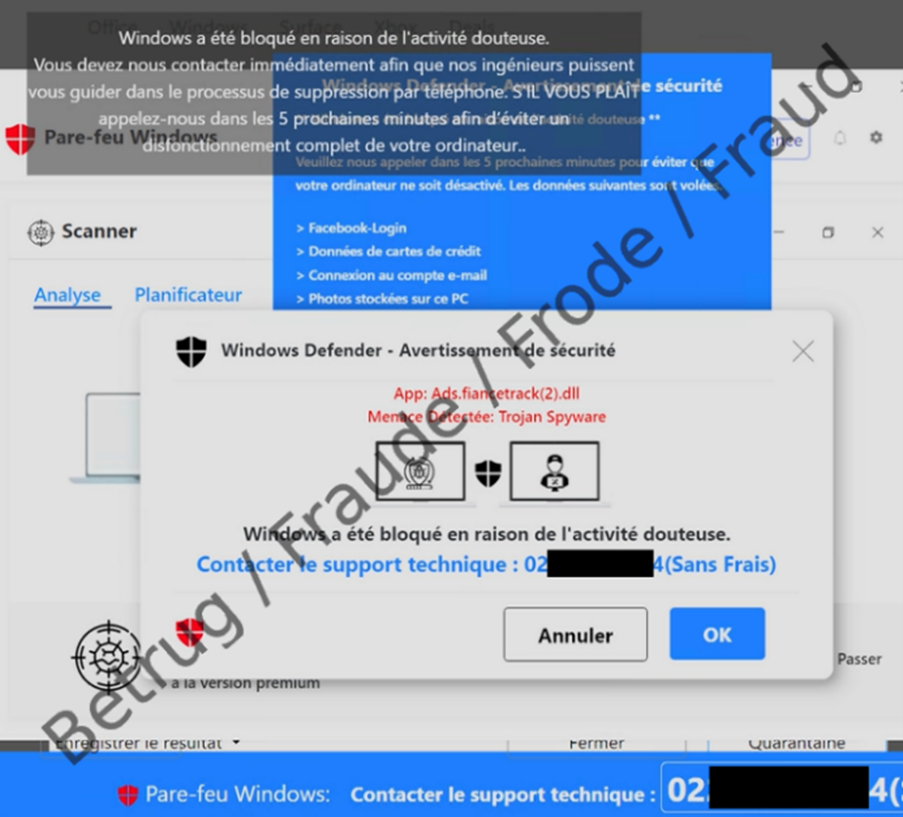
Here, however, it is not the perpetrator who calls the potential victim, but the other way round. A pop-up on the screen suggests to the victim that their device has been infected or blocked and needs to be cleaned by specialists. A Swiss telephone number is also provided, which they are told to call immediately.
This pop-up is sometimes even accompanied by an audible alert or voice recording indicating the alleged threat, thereby exerting additional pressure. However, the computer is not at risk in these cases and the problem can be solved by simply restarting the browser or device.
However, if you call the number given, an alleged support agent answers, usually in French. This person uses the remote maintenance programme installed by the victim to take control of the device. The victim is then asked, for example, to log into their e-banking account to pay for the alleged support service. The perpetrators then have full access and can make transfers to their own accounts.
It is also possible for malware such as a ‘keylogger’ to be installed allowing the fraudsters to track other entries made by the victim. Imagine that a file with the name ‘my-password.doc’ is on the victim's desktop – an easy way for the perpetrators to copy it.
Interestingly, reports of these incidents have so far mostly come from French-speaking Switzerland. Apparently, the pop-ups are only being targeted there or only become active if the browser language is French.
Cause and prevention
If a Swiss telephone number is used, the logical assumption is that the perpetrators are based in Switzerland and can therefore be identified Unfortunately, that is not the case, Skype numbers are usually used and the actual origin is concealed. However, by reporting the incident to the NCSC (https://www.report.ncsc.admin.ch/), including a screenshot of the display, the number can usually be deactivated quickly by the telecom provider.
But how do these pop-ups appear in the first place? Generally-speaking, the fraudulent pop-ups appear on websites that have been hacked or in fraudulent adverts via redirects. The victim simply clicks on an inconspicuous-looking link, e.g. in a spam mail or hit returned by a Google search.
Recommendations
- Do not allow strangers to pressure you into installing anything on your device;
- Do not grant strangers remote access to your device;
- If you see such a pop-up, take a screenshot (if necessary with your mobile phone) and send it to the NCSC;
- You can then close the browser or simply restart the device;
- If you have already granted remote access, your computer may already be infected. The first step is to uninstall the remote access programme;
- If you suspect your device has been infected, have the computer examined immediately by a specialist and cleaned if necessary. The safest option is to completely reinstall the computer’s operating system;
- If you have provided credit card details, contact your credit card company immediately to have the card cancelled;
- Do not make any banking transactions or online purchases with your credit card on the affected computer until you are sure that the computer is free of malware;
- Change any passwords that the caller may have obtained by accessing your device using the remote maintenance software.
Current statistics
Last week's reports by category:
Last modification 09.01.2024