04.06.2024 - Phishing websites have long been one of the cyber incidents most frequently reported to the National Cyber Security Centre (NCSC). In order to protect as many potential victims as possible, the NCSC tries to ensure these websites are deactivated as quickly as possible. Meanwhile, the fraudsters do everything they can to prevent this, as shown by an example reported to the NCSC last week.

Every day, thousands of new phishing pages are created and activated by fraudsters across the world. In addition, millions of phishing emails are sent out to entice victims into opening the fraudulent page and entering their credit card details or passwords. But security services, providers and registrars have also upped their game. Various processes have now been established to deactivate phishing websites as quickly as possible or to include them in filter programmes such as Google Safe Browsing. Speed is of the essence. Experience shows that most victims click on phishing pages in the first few hours after the fraudulent email is sent out. After a few hours, visitor numbers level off and the phishing page is useless.
The trick with the two-step procedure
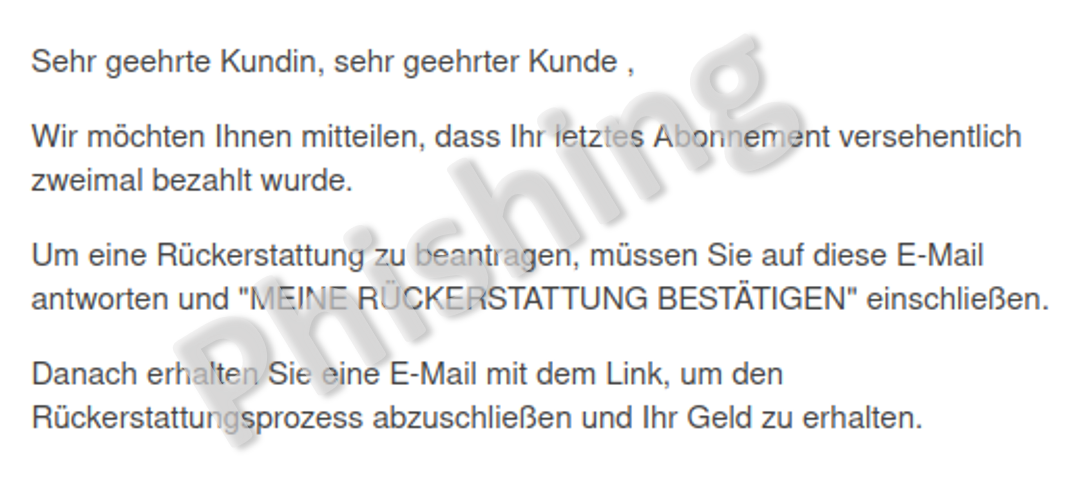
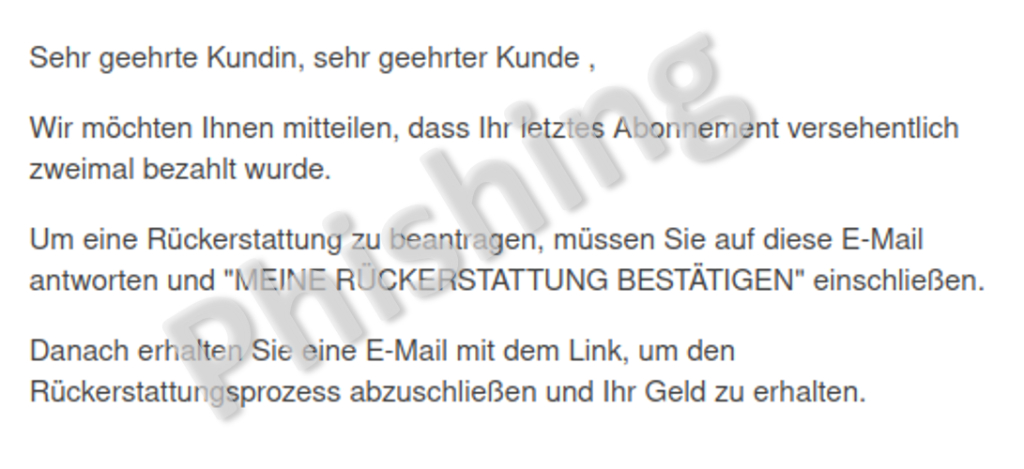
Fraudsters are therefore always looking for new ways to dodge the security authorities and prevent them from shutting down their phishing sites for as long as possible. Last week a phishing email was doing the rounds that uses a common trick. Instead of sending a phishing email asking the victim to click on a link that leads to a webpage, instead they are asked to reply directly to the email. The phishing link is sent in a second step. The idea is to prevent the vast majority of recipients – who immediately recognise the phishing attempt – from forwarding the email with link to security authorities such as the NCSC. This way, the fraudulent link is usually only sent to victims who do not recognise the attempt at fraud and therefore do not forward the link. This approach increases the likelihood that the site will remain online for longer, thus enticing more potential victims to enter their data.
In this way, the scammers also keep away people who recognise the phishing attempt and try to contaminate their data by entering false usernames and passwords. The fact that scammers are interested in keeping the data they obtain as clean as possible has already been explained in an earlier NCSC weekly review.
The trick with the browser agent
Scammers have a variety of other tricks to keep a phishing page online for as long as possible. For example, they exploit the fact that a large proportion of websites are now accessed via smartphones, especially by private users. They set up phishing websites in such a way that these can only be displayed on a smartphone. If someone tries to access the site from a desktop computer or laptop, a bona fide, unsuspicious page is displayed. The way it works technically is as follows. When someone accesses a website, a 'user agent' is active in the background. This is a software agent that transmits details of the user's operating system and browser so that the server can recognise the source of the request, i.e. Android device or iPhone, laptop or desktop computer. Most potential victims access websites via a smartphone, while the provider or security authorities, who are looking out for information indicating phishing websites, tend to be working on desktop computers. Because the phishing webpage has been set up in such a way that it only displays on a smartphone, it goes unnoticed by the analyst on the desktop computer and, in the worst case, no action is taken to shut it down the webpage.
Report phishing sites and phishing emails to the NCSC
The NCSC receives reports of phishing via various channels. You can report phishing websites or emails containing phishing links via the NCSC-operated platform antiphishing.ch. If you wish to receive a response or explanation, please complete the form available at https://www.report.ncsc.admin.ch.
Further recommendations
- No bank or credit card company will ever send you an email requesting that you change your password or verify your credit card details.
- Never divulge personal data such as passwords or credit card details on a website that you accessed by clicking on a link in an email or text message.
- Bear in mind that email sender IDs can easily be spoofed.
- As soon as you realise that you have entered your password on a phishing site, change this password for all services where you use it.
- If you provided credit card details, contact your credit card company immediately to have the card blocked.
- In the case of an email password, you should also reset all passwords for web service providers that are linked to this account.
Current statistics
Last week's reports by category:
Last modification 04.06.2024