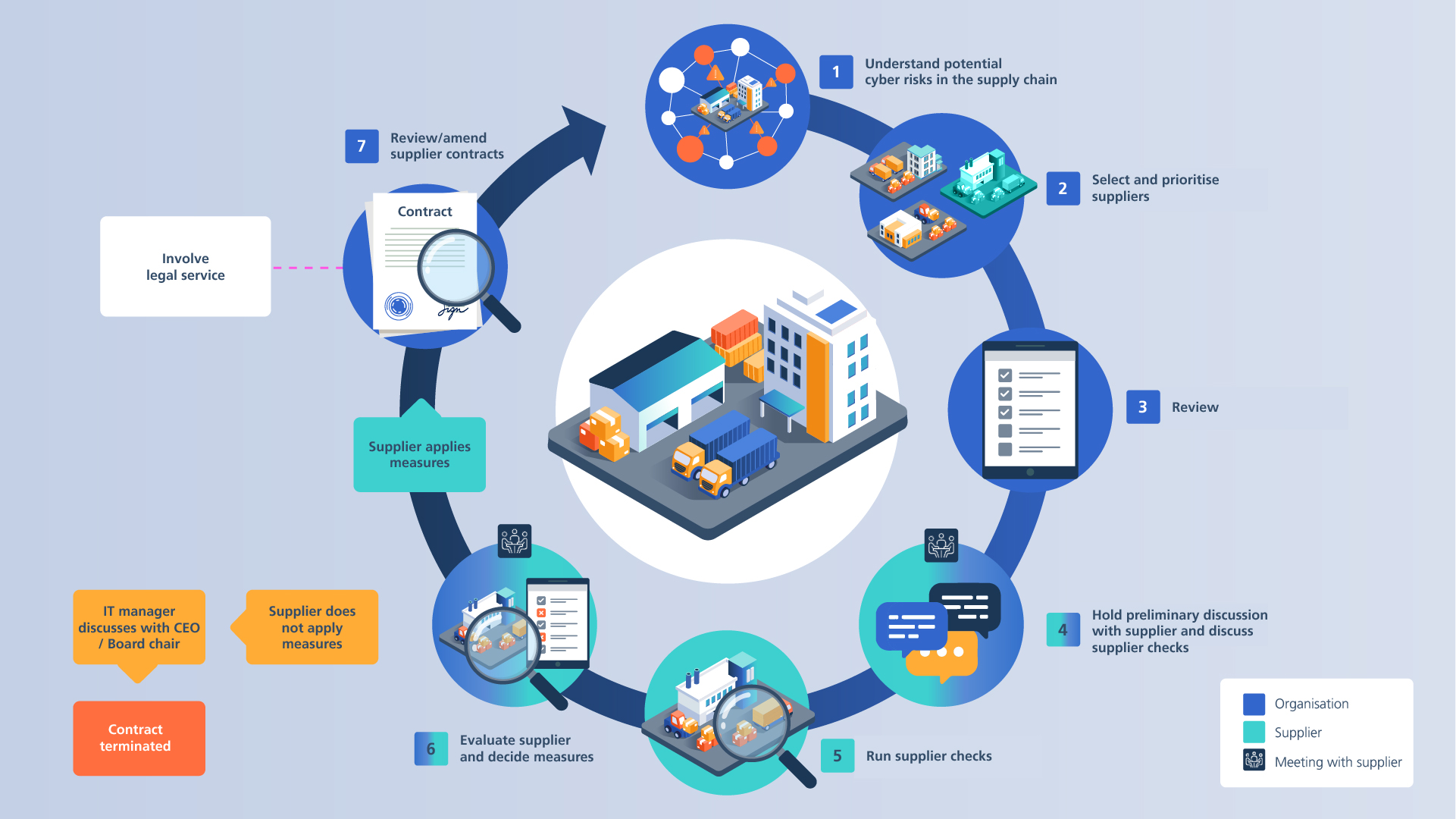
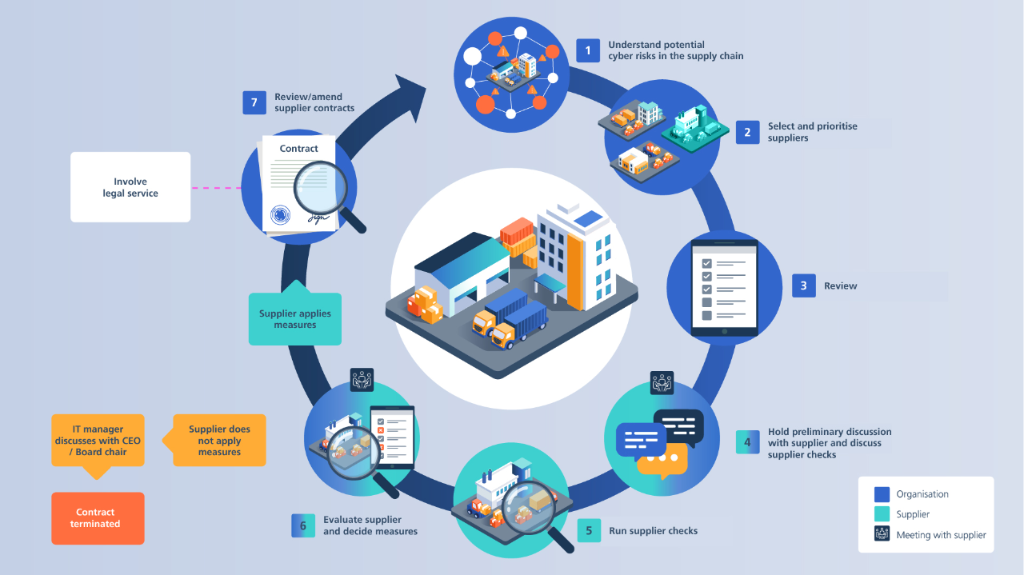
To mitigate cybersecurity risks along the supply chain, organisations need to understand and assess their risks, define their requirements and specifications for their suppliers, subcontractors and providers, and verify compliance. To this end, companies, public authorities and organisations should take a strategic approach to cybersecurity risks in their IT/OT supply chain. This is known as Cyber Supply Chain Risk Management (C-SCRM).
Ideally, the strategy is based on a continuous review of all dependencies in the IT/OT supply chain. The United States' National Institute of Standards and Technology (NIST) has published a helpful publication and key practices (NISTIR 8276).
Pilot project with Planzer Transport AG
To enable companies, authorities and organisations in Switzerland to pragmatically implement their supply chain cybersecurity requirements, the National Cyber Security Centre (NCSC) has conducted a pilot project with Planzer Transport AG and developed an easy-to-understand process and specific resources. Feedback on the pilot project is being collected continuously via a feedback form.
Measures to protect against cyberattacks in the supply chain
1. Know your supply chain and be aware of cyber risks

Supply chains often span many companies around the world. In order to be able to manage risks arising from the relationship between suppliers and their subcontractors or from other technical and non-technical influences, maximum transparency should be the goal.
A good understanding of your own IT/OT supply chain will help you to recognise how the use of external suppliers and service providers could expose your organisation and your end customers to cyber risks.
2. Selecting and prioritising suppliers

Choosing the right suppliers, subcontractors and providers is an important first step in ensuring your organisation can operate safely. Identifying the business impact of each of your suppliers will help you prioritise them. The pilot project distinguishes between three types of suppliers:
- Partners who, due to their privileged access to your organisation's internal systems, could have a negative impact on your IT/OT. For example: partners who are responsible for operating a system in your organisation's network.
- Partners who provide hardware or software to your organisation that could cause damage if compromised. For example: Microsoft Office or other specialised applications or systems operated by your organisation.
- Partners who provide key services to your organisation that, if discontinued or interrupted, would affect the confidentiality, availability or integrity of data. For example: SaaS, logistics or outsourcing partners such as service desks or product suppliers.
In order to prioritise your suppliers, you need to know what cyber risks they face, what dependencies exist and what information you share with them. To help your organisation ask the right questions and take targeted action to strengthen your cyber resilience, the National Cyber Security Centre (NCSC) has worked with Planzer Transport AG to develop a set of key questions.
3. Review of the current situation

In this step, your IT/OT Manager reviews and assesses the current situation in your organisation. If necessary, your company's own protective measures can be improved and brought up to date at this stage.
4. Preliminary meeting with suppliers and discussion of supplier review

In this step, you can adapt the key questions for each of your suppliers. Reviewing the key questions is a good way to prepare for the preliminary supplier meeting. These meetings will raise awareness of cybersecurity in the supply chain with your suppliers. In addition, if necessary, you can go through the key questions together and your organisation can offer its support.
5. Supplier review

You can mitigate cybersecurity risks in your supply chain by maintaining close contact with your suppliers and implementing appropriate controls where necessary. Planzer Transport AG's experience has shown that the only way to improve conditions in your own supply chain is for your suppliers to recognise the need for change and to understand how it will benefit their business. Supply chain management should therefore focus on building supplier expertise. There are two approaches to performing a supplier review: self-assessment and on-site inspections.
Self-assessments are a good first step and can be followed up with on-site visits or audits, for example. The decision to carry out an audit is based on the assumption that suppliers are unwilling to implement customer requirements and therefore need to be monitored. Planzer Transport AG's practical experience shows that suppliers generally want to implement requirements, but may not be in a position to do so or may need to be incentivised. To help your organisation ask the right questions of your suppliers, the National Cyber Security Centre (NCSC) has worked with Planzer Transport AG to develop a set of key questions.
6. Evaluating the supplier review / defining measures

In this step, the supplier's self-assessment is evaluated by your organisation. If you find that your requirements are not being met, your supplier needs to make improvements. The aim of the supplier review is to improve the performance and cyber resilience of your suppliers.
7. Supplier contracts

If the supplier review is successful, the next and final step in the process is to create or review/adapt the contracts. A supplier contract is a legally binding agreement between your organisation and the supplier, and should include provisions to ensure compliance with information security and privacy regulations. It covers issues such as liability, quality requirements and delivery modalities.
Additional links:
- Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations (nist.gov)
- NISTIR 8276 Key Practices in C-SCRM | CSRC
- Richtlinie EU: L_2022333DE.01008001.xml (europa.eu)
- ISO - ISO 9001 and related standards — Quality management
- CCMv4.0 Auditing Guidelines | CSA (cloudsecurityalliance.org)
Last modification 01.01.2024